So you installed a VPN. Paid a few bucks for a subscription, downloaded the app, pressed the big green "Connect" button, and now you feel like an invincible digital ninja. I hate to break it to you, but you're not a ninja. You're someone who bought an invisibility cloak on AliExpress and genuinely wonders why people can still see them.
How Your Computer Leaks Data
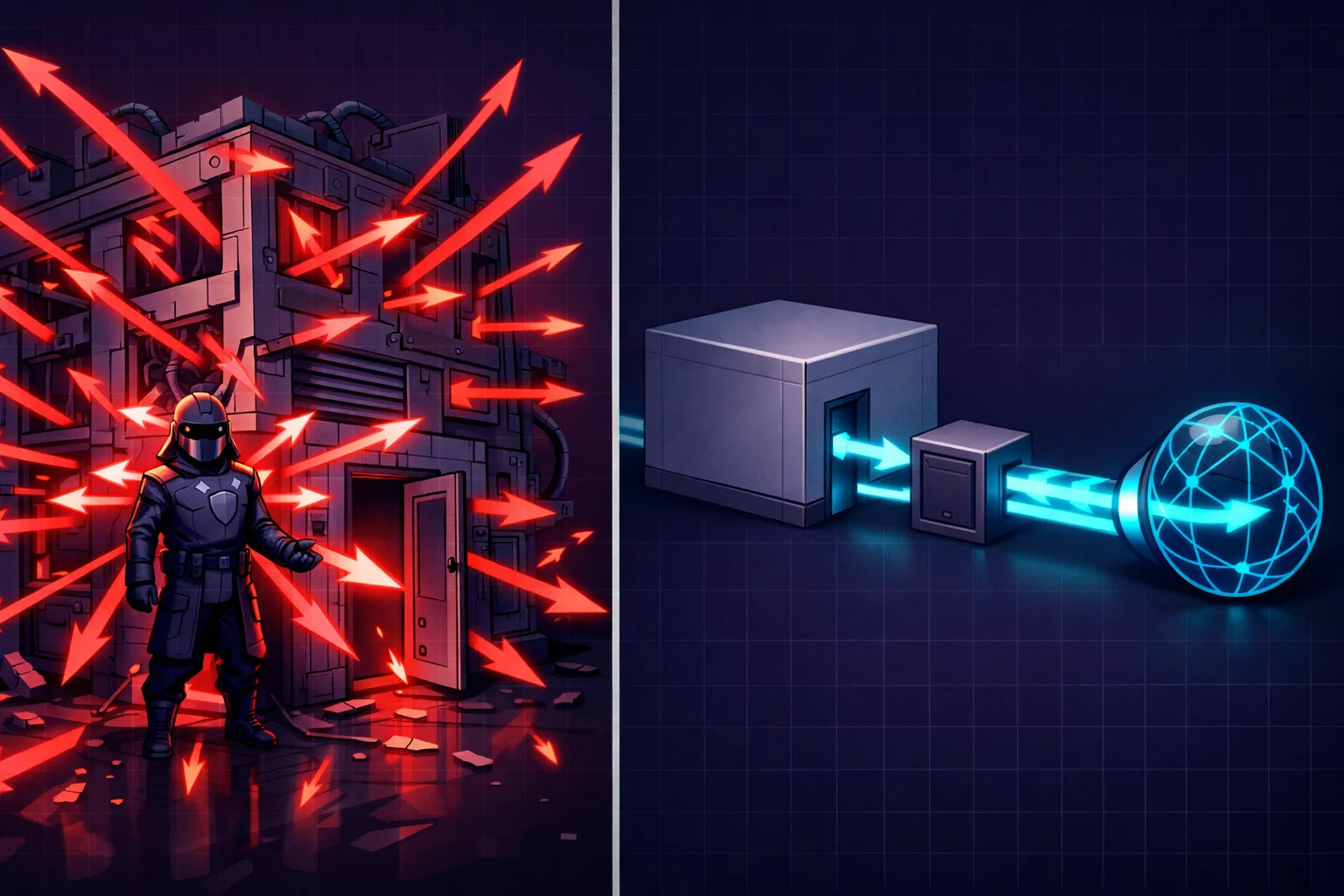
Think of your computer as an apartment building. There's one exit to the street — the network interface. Through this door, all the tenants go out to the internet: browser, email client, Telegram, Windows system services that report to Microsoft every five minutes about what you're doing, and another hundred programs you don't even know about. VPN in this analogy is a security guard at the door. He tells all tenants: "Hey, go through me, I'll escort you through a secret tunnel." And most tenants comply.
But here's the problem. He's just a guard. He didn't brick up the windows. He didn't concrete over the back door. He just stands there and politely asks. And some tenants — especially those with administrator privileges — can tell him to piss off and jump out the window.
The Moment of Truth: Reconnect
Your VPN disconnected for a second. Maybe the server hiccuped. Maybe your internet glitched. One second. What happens? The guard passed out, the door is wide open, and all programs happily ran outside directly. The browser sent a request. The torrent client told the tracker "hey, here's my real IP." Windows telemetry reported your location. One second — and you're exposed.
"But I have a kill switch!" you'll say. A kill switch is a program that's supposed to notice that another program crashed and quickly block all traffic. A program. That's supposed to react faster than other programs can send packets.
Route Racing and IPv6
Computer turned on. Network came up. Internet works. And VPN? VPN is still loading. It's in autostart, but autostart means "after the system decides it's ready." During these few seconds, your traffic goes directly. System services are already checking for updates. Browser is pulling your open tabs. Messengers connected to servers. You haven't even made your tea yet, and your IP is already logged across half the internet.
And here's another gift: while you were setting up VPN for IPv4, everyone forgot about IPv6. It runs in parallel — separate protocol, separate address, separate route. A site requested an AAAA record — and got your real IPv6 address while you sat behind a VPN thinking you were invisible. It's like wearing a mask on your face but pinning a name badge to your chest.
Aside: VPN on the Router
Before moving to the main solution, let me tell you about an intermediate option. You can set up VPN not on the computer, but on the router. I have a Keenetic with WireGuard. All home network traffic goes through the tunnel before it even reaches any device. The laptop doesn't even know there's a VPN — it just connects to the router and thinks it's regular internet.
Programs on the computer can't bypass the tunnel — they don't know about it. No route racing at startup — the router is already running. Malware with admin rights can't disable VPN — it's on a different device. This is no longer an AliExpress invisibility cloak. Takes ten minutes to set up, works reliably, I recommend at least trying it.
Whonix and the Problem with Tor
Whonix consists of two virtual machines: Gateway and Workstation. The first one is connected to the internet. The second is connected ONLY to Gateway through an internal network. Workstation has physically no internet access — no route, no way to send a packet past Gateway. This isn't a guard at the door — it's a room with no doors or windows, where the only exit leads through the gateway. Brilliant, paranoid, works. But I won't write three pages about Whonix — there's already so much written about it that another article would be information garbage. Want details — go to whonix.org.
Now about what paranoids don't like to talk about. Tor is painfully slow. Three nodes, each with its own ping. Open a page — wait. Download a file — make some tea. Watch a video — forget it. Half the internet blocks Tor exit nodes. Google asks for captcha. Cloudflare shows endless checks. Banks deny access. For regular daily work, Tor doesn't cut it. Nobody's going to surf through Tor on a home computer — that's masochism.
And let's be honest: if someone really wants to find you — they will. Intelligence agencies with budgets, control over entry and exit points, access to logs — they'll find a way. But we're not here for perfect anonymity. We're here to make things simple, convenient, and hassle-free. To stop traffic from leaking on reconnect and prevent malware from bypassing the tunnel.
The Solution: Whonix Principle + Normal VPN
We take Whonix architecture — physical isolation, no leaks. But instead of Tor, we put a fast VPN to our own server. Here's how it looks: a separate machine (let's call it Gateway) is connected to the internet and to your VPN server via sing-box or any other client. Your work computer is connected only to Gateway and uses it as a gateway. Gateway is configured to only pass traffic through the VPN tunnel. Everything else — DROP. No tunnel — no internet.
Gateway is simply a gateway machine with two network interfaces: one faces the internet, the other faces the internal network. It can be a VM in VirtualBox or Proxmox, a Raspberry Pi, an old laptop, a mini-PC for fifty bucks — doesn't matter what it runs on, what matters is how it's configured. Gateway runs a VPN client (sing-box handles all modern protocols: VLESS, VMess, Shadowsocks, WireGuard), and firewall rules are set so that all incoming traffic from the second interface only goes through VPN, direct exit is blocked.
Your Computer and Why This Works
No Linux VMs needed. Your work computer is Windows, Mac, whatever. You simply set Gateway as the default gateway in network settings: manually enter the IP, or set up DHCP on Gateway and everything configures automatically. That's it — your computer now accesses the internet through Gateway, and Gateway only allows VPN.
A VPN client on the computer is software — it can be bypassed, disabled, it can crash. Gateway is network topology. Your computer is physically connected only to the internal network, the only route out is through Gateway, and Gateway only releases through VPN. VPN disconnected? Your computer loses internet — doesn't leak IP, loses internet, because there's no other path. Malware got admin rights? It can do whatever it wants on your computer, but it can't bypass VPN — there's nowhere to go.
What This Doesn't Solve and Conclusion
If the Gateway host is compromised — everything's useless. VPN provider or hoster sees the connection — choose trustworthy ones. Human factor: logged into a personal account — you exposed yourself. But we're not building an NSA bunker here. We're making sure traffic doesn't leak on reconnect and malware can't bypass the tunnel. This setup solves that task completely.
A VPN client is a program, programs can be bypassed, disabled, tricked. VPN on a router is better. Gateway with isolation is architecture — you can't bypass a route that doesn't exist, and you get normal speed because it's VPN, not Tor. If you're curious how this works — now you understand the principle. If you need to set it up — below is a prompt for an AI that will give you step-by-step instructions for your specific situation. I'm not going to write configs here — they'll get outdated, everyone has different systems, and nobody's going to read them anyway. An AI will do it better and specifically for you.
Setup Prompt
Copy this prompt into ChatGPT, Claude, or another AI. Fill in the parameters in square brackets.
I need step-by-step instructions for setting up a VPN gateway for traffic isolation.
Goal: all traffic from my work computer should go through a separate gateway machine that only allows VPN. If VPN drops — internet should stop working, not go directly.
My parameters:
Gateway:
- Platform: [VirtualBox VM / Proxmox VM / Raspberry Pi / mini-PC / old laptop]
- OS on Gateway: [Debian / Ubuntu / Alpine / other]
- VPN protocol: [VLESS / VMess / WireGuard / Shadowsocks / other]
- VPN server address: [already have my own VPS / need to set up server first]
- VPN client: [sing-box / xray / other]
Work computer:
- OS: [Windows 10 / Windows 11 / macOS / Linux]
- How it will connect to Gateway: [through virtual network in the same hypervisor / through physical cable / through separate Wi-Fi network]
Give me:
1. Gateway setup:
- OS installation (brief, no fluff)
- Configuring two network interfaces (one to internet, one to internal network)
- Installing and basic configuration of VPN client
- Firewall rules: traffic from internal interface goes ONLY through VPN tunnel, direct internet exit is blocked
- Enabling packet forwarding
2. Work computer setup:
- How to set Gateway as default gateway
- Or how to set up DHCP on Gateway so settings are distributed automatically
3. Verification:
- How to confirm traffic goes through VPN (what IP shows)
- How to verify that when VPN stops on Gateway, internet on work computer stops rather than going directly
Give me specific commands and configs. No long explanations — I understand what I'm doing, I just need the commands.